
|
Training, Open Source Programming Languages |
| Home | Accessibility | Courses | The Mouth | Resources | Site Map | About Us | Contact |
| For 2023 (and 2024 ...) - we are now fully retired from IT training. We have made many, many friends over 25 years of teaching about Python, Tcl, Perl, PHP, Lua, Java, C and C++ - and MySQL, Linux and Solaris/SunOS too. Our training notes are now very much out of date, but due to upward compatability most of our examples remain operational and even relevant ad you are welcome to make us if them "as seen" and at your own risk. Lisa and I (Graham) now live in what was our training centre in Melksham - happy to meet with former delegates here - but do check ahead before coming round. We are far from inactive - rather, enjoying the times that we are retired but still healthy enough in mind and body to be active! I am also active in many other area and still look after a lot of web sites - you can find an index ((here)) |
|
Setting up your Linux system as a firewall using iptables
During last week's Linux course (a private one) we took a look at firewalls using iptables. iptables can be run on an individual Linux machine, controlling the traffic that's allowed in and out, and turning that machine into its own firewall: * INPUT rules control the outside agents that can contact (or attempt to contact) services running on the firewalled systsm * OUTPUT rules control the services (and locations of services) that users of the machine can contact, or attempt to contact iptables can also (usually more commonly and usefully) be run on a gateway machine - a Linux machine with multiple interfaces, where additionally you can specify: * FORWARD rules control the service and ports that can be passed through the machine from one network to another, without being subjected to both the input and the output rules. 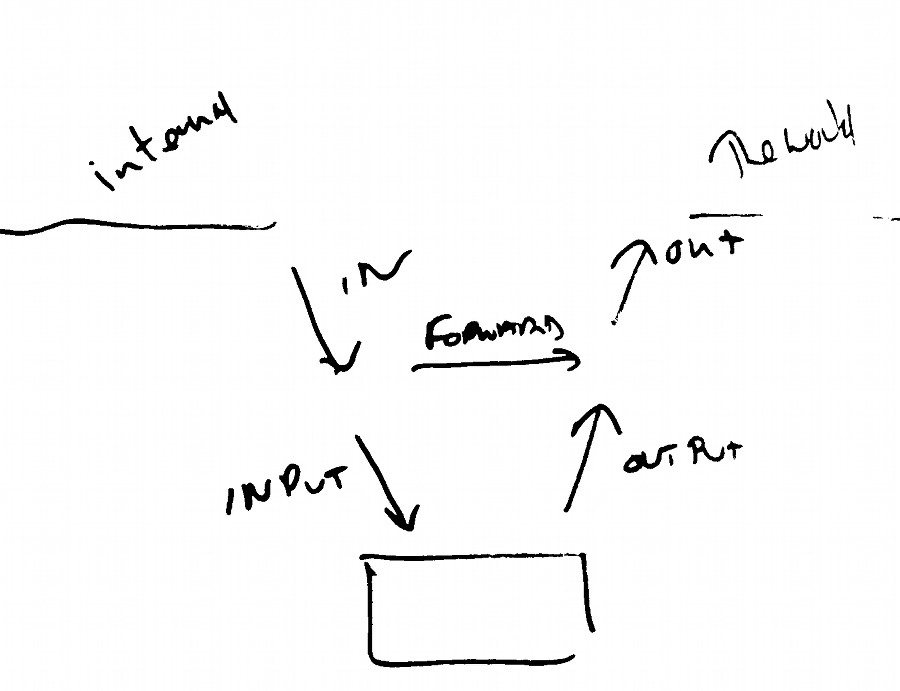 The three routes that you can control on a firewall. Rules are specified based on each interface, so in addition to my set of three shown on the diagram, there will be another set of three controlling traffic from the world into your network, and don't forget the local loopback adapter too. There's a sample configuration file [here] which demonstrates some first principles, using a machine with a single external connection. The three routes that you can control on a firewall. Rules are specified based on each interface, so in addition to my set of three shown on the diagram, there will be another set of three controlling traffic from the world into your network, and don't forget the local loopback adapter too. There's a sample configuration file [here] which demonstrates some first principles, using a machine with a single external connection.Let's set up our machine so that we: * Allow the user of the machine to make use of any external services (s)he may want to contact * Restrict incoming requests to a limited number of carefully selected services on a potentially dirty and dangerous network Step 1 - set up the basic rules: iptables -P INPUT DROPWe're starting from a default in our machine where nothing is allowed in, anything is allowed out, and nothing is forwarded. DROP means that our system pretends that there isn't a system there at all, rather than sending back any sort of response to say "go away". Step 2 - once traffic has been allowed, allow it to continue iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPTWe're now modifying the input rule. If we get an input as a result of an outgoing question we've asked, we need to get that answer back, which wouldn't happen if we left the input rule unmodified. Step 3 - allow additional incoming services This is optional and only needed if your machine's to be a server. The sample file (link above) allows ssh, DNS, Ldap and FTP traffic on their default ports. It also allows port 80 (web server / http) traffic. Here are some of the extra iptables ommands (the ssh and http ones): iptables -A INPUT -p tcp --dport ssh -i eth0 -j ACCEPTFor some of these services, you'll need multiple ports, and perhaps to allow udp traffic as well as tcp. Step 4 - allow local loopback Every Linux box will have multiple services running, and these may want to contact each other within the system. For example, your local web server (which can be contacted using the rule above from outside) may want to contact a MySQL daemon that can't be accessed directly from outside: iptables -A INPUT -i lo -j ACCEPTPotentially, this is a vital rule - all sorts of standard bits of software contact each other via the loopback adaptor, and failure to specify this additional rule can result in quite a few things not working. Step 5 - allow pings Optional, again. Do you want your machine to respond to pings? The sample file contains the lines you need to do this, while looking to configure ping in such a way that you don't get flooded when handling aggressive external (flood) pinging. Please note - setting up a firewall is NOT your total answer to "security"!. Although we have restricted traffic in our example to services of our choice, we have not considered the security of each of the individual services we have allowed through. We need to consider the security of each of those allowed services individually, including the possibility of security breaches which use those services as their means of transport - for example, an injection attack to a database which uses a flaw (written 2012-04-02, updated 2012-04-07) Associated topics are indexed as below, or enter http://melksh.am/nnnn for individual articles A192 - Web Application Deployment - Firewalls[770] Splash! - (2006-06-20) [806] Check your user is human. Have him retype a word in a graphic - (2006-07-17) [3680] How can I run multiple web servers behind a single IP address? - (2012-04-02)
Some other Articles
Weak references in Lua - what are they, and why use them?Melksham Business Newsreel Kicking up a stink, the Victorian way? Setting up your Linux system as a firewall using iptables Potteries and Staffordshire in the Sunshine Some advise for guest speakers at meetings Rising prices, changing habits and society Spring 2012 Off to walk the dogs |
4759 posts, page by page
Link to page ... 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48, 49, 50, 51, 52, 53, 54, 55, 56, 57, 58, 59, 60, 61, 62, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 91, 92, 93, 94, 95, 96 at 50 posts per pageThis is a page archived from The Horse's Mouth at http://www.wellho.net/horse/ - the diary and writings of Graham Ellis. Every attempt was made to provide current information at the time the page was written, but things do move forward in our business - new software releases, price changes, new techniques. Please check back via our main site for current courses, prices, versions, etc - any mention of a price in "The Horse's Mouth" cannot be taken as an offer to supply at that price.
Link to Ezine home page (for reading).
Link to Blogging home page (to add comments).
PH: 01144 1225 708225 • EMAIL: info@wellho.net • WEB: http://www.wellho.net • SKYPE: wellho
PAGE: http://www.wellho.net/mouth/3679_Set ... ables.html • PAGE BUILT: Sun Oct 11 16:07:41 2020 • BUILD SYSTEM: JelliaJamb