
|
Training, Open Source Programming Languages |
| Home | Accessibility | Courses | The Mouth | Resources | Site Map | About Us | Contact |
| For 2023 (and 2024 ...) - we are now fully retired from IT training. We have made many, many friends over 25 years of teaching about Python, Tcl, Perl, PHP, Lua, Java, C and C++ - and MySQL, Linux and Solaris/SunOS too. Our training notes are now very much out of date, but due to upward compatability most of our examples remain operational and even relevant ad you are welcome to make us if them "as seen" and at your own risk. Lisa and I (Graham) now live in what was our training centre in Melksham - happy to meet with former delegates here - but do check ahead before coming round. We are far from inactive - rather, enjoying the times that we are retired but still healthy enough in mind and body to be active! I am also active in many other area and still look after a lot of web sites - you can find an index ((here)) |
|
Injection Attack if register_globals in on - PHP
You may have heard me talk about "injection attacks" and that having register_globals set to on in PHP makes you liable to be caught by them. Well - that's a little bit dramatic as you can write perfectly safe PHP scripts with the setting on if you're careful. Here's an example of a script which is not secured ... <?phpNow the output SHOULD look like this: 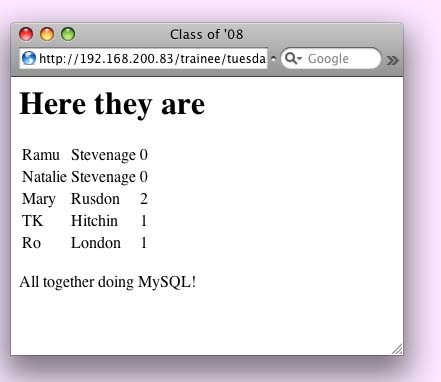 But I can make it look like this ... VERY easily! 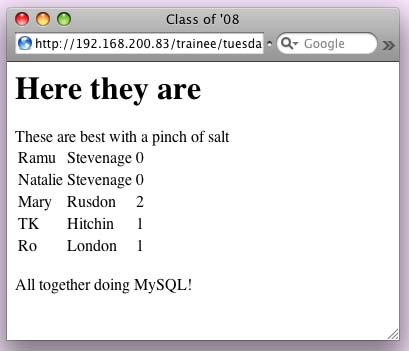 Did you spot the extra line of text?. What has happened? I have used the $table variable to build up my table, using the "dot equals" operator. Fine - except that I have used it the very first time that the variable is references which means that in inherits any form values that are input via a box called table on the form that calls up the script. So all I have to do is to write such a form and I can add whatever I like at that point .. which could just be text ... or it might be Javascript I want echoed out, font changes, code to call up an image .... The solution is to change the first "dot equals" into just "equals". That's the good programming solution. But turning register_globals off also solves the problem, as the variable would not then be populated from the form. The best solution? do both!. (written 2009-02-04) Associated topics are indexed as below, or enter http://melksh.am/nnnn for individual articles H312 - PHP - Tips and Techniques[789] Hot answers in PHP - (2006-07-02) [917] Syntax checking in PHP - (2006-11-07) [1010] Dates, times, clickable diarys in PHP - (2006-12-28) [1270] PHP Standalone - keyboard to screen - (2007-07-18) [1649] Easy conversion - image formats, currencies and distances - (2008-05-21) [1667] Checking server performance for PHP generated pages - (2008-06-06) [1684] Two PHP include files to make easy web site indexing and navigation - (2008-06-21) [1958] PHP - Parse error: syntax error, unexpected $end ... - (2008-12-23) [1983] Keeping PHP code in database and running it - (2009-01-09) [2274] PHP preg functions - examples and comparision - (2009-07-08) [2478] How did I do THAT? - (2009-10-26) [2981] How to set up short and meaningfull alternative URLs - (2010-10-02) [4074] A comment on comments in PHP - (2013-04-28) [4310] Problem ... I want to print a series of numbered forms - (2014-10-05) [4319] PHP - some quick fixes if scripts have issues, and how to use our support - (2014-11-19) [4426] FileMaker Day to Unix Time conversion - (2015-02-15) [4621] The power of scripting - (2016-01-12) H117 - Security in PHP [345] Spotting a denial of service attack - (2005-06-12) [426] Robust checking of data entered by users - (2005-08-27) [920] A lion in a cage - PHP - (2006-11-10) [947] What is an SQL injection attack? - (2006-11-27) [1052] Learning to write secure, maintainable PHP - (2007-01-25) [1086] Injection attacks - safeguard your PHP scripts - (2007-02-20) [1323] Easy handling of errors in PHP - (2007-08-27) [1387] Error logging to file not browser in PHP - (2007-10-11) [1396] Using PHP to upload images / Store on MySQL database - security questions - (2007-10-19) [1482] A story about benchmarking PHP - (2007-12-23) [1542] Are nasty programs looking for security holes on your server? - (2008-02-17) [1679] PHP - Sanitised application principles for security and useability - (2008-06-16) [1694] Defensive coding techniques in PHP? - (2008-07-02) [1747] Who is watching you? - (2008-08-10) [1779] Injection Attacks - avoiding them in your PHP - (2008-08-31) [2628] An example of an injection attack using Javascript - (2010-02-08) [2688] Security considerations in programming - what do we teach? - (2010-03-22) [2939] Protecting your images from use out of context - (2010-08-29) [3210] Catchable fatal error in PHP ... How to catch, and alternative solutions such as JSON - (2011-03-22) [3698] How to stop forms on other sites submitting to your scripts - (2012-04-15) [3747] An easy way to comply with the new cookie law if your site is well designed - (2012-06-02) [3813] Injection Attacks - PHP, SQL, HTML, Javascript - and how to neutralise them - (2012-07-22) [4642] A small teaching program - demonstration of principles only - (2016-02-08) H110 - PHP - HTML Web Page Data Handling [50] Current cost in your local currency - (2004-09-16) [589] Robust PHP user inputs - (2006-02-03) [896] PHP - good coding practise and sticky radio buttons - (2006-10-17) [1001] .pdf files - upload via PHP, store in MySQL, retrieve - (2006-12-19) [1053] Sorting people by name in PHP - (2007-01-26) [1136] Buffering output - why it is done and issues raised in Tcl, Perl, Python and PHP - (2007-04-06) [1169] Emailing as HTML (Web Page) - PHP example - (2007-04-30) [1831] Text formating for HTML, with PHP - (2008-10-11) [2046] Finding variations on a surname - (2009-02-17) [2107] How to tweet automatically from a blog - (2009-03-28) [2135] What features does this visitors browser support? (PHP) - (2009-04-22) [3036] Sending out an email containing HTML from within a PHP page - (2010-11-07) [3926] Filtering PHP form inputs - three ways, but which should you use? - (2012-11-18)
Some other Articles
Also for the eyes of the catThings people say on the phone Who sticks by you in the snow? Melksham Climate Friendly Group Injection Attack if register_globals in on - PHP Carry on Training - in spite of the weather sw_vers - what version of OSX am I running? Pre and post increment - the ++ operator Short health and safety course Learning Python - many new example programs |
4759 posts, page by page
Link to page ... 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48, 49, 50, 51, 52, 53, 54, 55, 56, 57, 58, 59, 60, 61, 62, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 76, 77, 78, 79, 80, 81, 82, 83, 84, 85, 86, 87, 88, 89, 90, 91, 92, 93, 94, 95, 96 at 50 posts per pageThis is a page archived from The Horse's Mouth at http://www.wellho.net/horse/ - the diary and writings of Graham Ellis. Every attempt was made to provide current information at the time the page was written, but things do move forward in our business - new software releases, price changes, new techniques. Please check back via our main site for current courses, prices, versions, etc - any mention of a price in "The Horse's Mouth" cannot be taken as an offer to supply at that price.
Link to Ezine home page (for reading).
Link to Blogging home page (to add comments).
PH: 01144 1225 708225 • EMAIL: info@wellho.net • WEB: http://www.wellho.net • SKYPE: wellho
PAGE: http://www.wellho.net/mouth/2025_Inj ... n-PHP.html • PAGE BUILT: Sun Oct 11 16:07:41 2020 • BUILD SYSTEM: JelliaJamb